Introduction to Domain Trusts
The purpose of this article is explaining the basics of domain trusts within Active Directory.
Imagine two nations allowing their citizens to visit each other. A trust is like a treaty between them stating who can visit and what they can do.
Main Ideas
Domain Trust: An agreement that permits users in one domain to access resources in another.
Connection with Authentication Systems: It's similar to having a visa for entering another country because both nations trust each other's citizen verification process.
Types of Domain Trusts
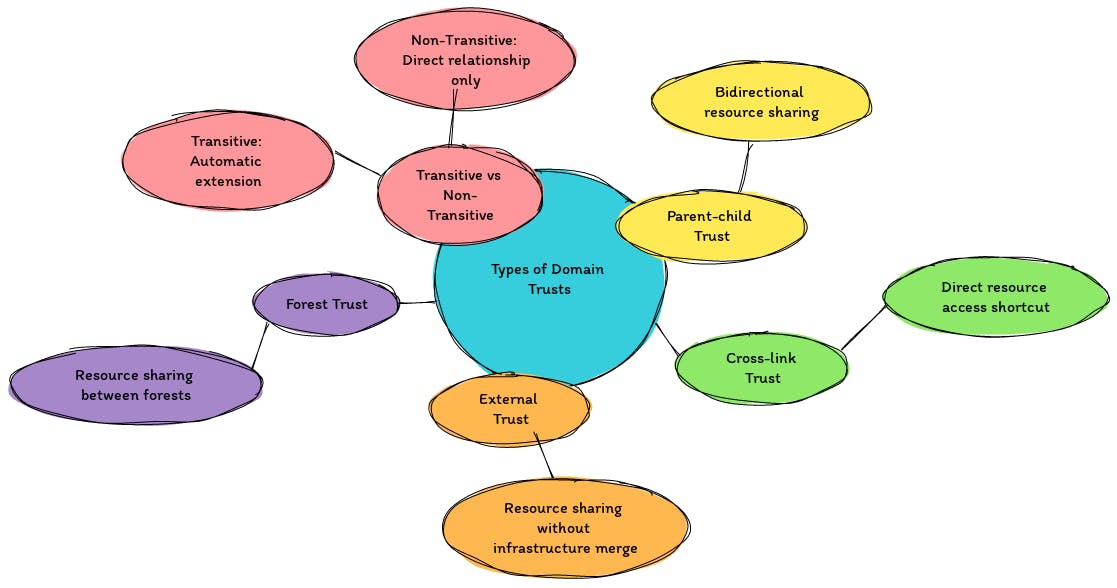
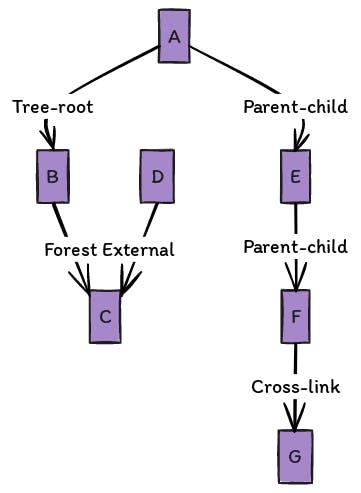
Parent-Child Trust: Think of it as the default relationship between a parent company and its subsidiary, where resources are shared both ways.
Shortcut Trust: This serves as a shortcut for direct resource access between two subsidiaries without involving the parent company.
External Trust: Envision two companies agreeing to share resources without merging their entire infrastructures.
Forest Trust: When two different forests (collections of domains) decide to share resources.
Transitive vs. Non-Transitive: Refers to whether a trust extends to other trusts (transitive) or remains limited to the direct relationship (non-transitive).
Establishing and Managing Domain Trusts
Below are step by step guidance about on the setup and maintenance of trusts with a focus on security.
Step-by-Step Guidance
Assessing Need and Security: Prior to creating a trust, assess its necessity and potential security implications.
Establishing Trusts: Follow instructions on how to set up each type of trust within Active Directory.
Ensuring Security: Regularly assess trust relationships to confirm their necessity and security.
Common Challenges and Security Considerations
This section is to identify mistakes in configuring trusts and strategies for addressing security risks.
Typical Mistakes
Creating trusts that expose sensitive resources.
Neglecting to remove or update trusts following mergers or acquisitions.
Troubleshooting
Steps for auditing existing trusts and implementing measures like SID filtering to enhance security, along with reviews of trust relationships.
Best Practices
Principle of Least Privilege: Grant access as needed for tasks.
Regular Audits: Periodically review trusts to ensure they are still essential and secure.